Technological advancements have changed face of warfare through battlefield networks but have also introduced vulnerabilities
 Col Mandeep Singh (retd)
Col Mandeep Singh (retd)
The single most important activity in war is command and control. It cannot by itself drive home an attack against the enemy or thwart one that is launched against its own troops. It does not destroy any target, provide supplies or carry out a medical evacuation. Yet without command and control none of these or any other military activity will be possible. Without command and control armies will be reduced to mobs carrying out random acts of violence. It is only with command and control that commanders can optimise their resources so that a military force performs its task in an organised manner towards a stated goal.
Command and control is something that commanders do. It includes, but is not limited to, gathering and analysing information, making decisions, organising resources, planning, communicating instructions, coordinating, monitoring results and supervising execution. With time and technological advances, the instruments of exercising command and control have evolved and expanded to encompass communications, computers, intelligence, surveillance and reconnaissance. Within this, battlefield networks are used to detect what is happening on the ground, process that data into actionable information, decide on a course of action, communicate decisions among forces, act on those decisions and assess the effectiveness of the actions taken.
It is important to understand that this process is sequential and not conforming to it can lead to lapses and errors with deadly results. A decision should be taken only after the information has been processed. Similarly, action should not precede the decision.
Battlefield Networks
Primarily, a battlefield network is a combination of target acquisition sensors, target localisation sensors, command and control (C2) elements, weapons, weapon platforms, and electronic communications linking them together. Battle networks are also referred to as the ‘sensor-to-shooter kill chain,’ or just the ‘kill chain.’
This system, or the network, is not a new phenomenon though the components of the same have changed over time. While scouts and couriers were used earlier, satellites, drones and aircraft do the task of reconnaissance now. Similarly, semaphore flags, telegraph and field telephones have largely been replaced by more modern communication systems. The new systems have given the capabilities to look and strike deeper but this capability, coupled with speed and ubiquity of communications, means that there is an exponential increase in the amount of information being generated by sensors that needs to be processed in time before arriving at a decision. This puts a lot of pressure both on the network and the commander, and poses some major challenges.

Better Options
The objective of a battlefield network is to enable better options for commanders, speed up the decision making process and optimise effects in the battlespace. This is achieved by connecting platforms and systems across domains by seamlessly passing surveillance, targeting, damage assessment, and other information from one platform to another to improve the accuracy, range, persistence, and speed of effects. As the network integrates more platforms, sensors, communication paths and other nodes, the efficiency increases in a nonlinear manner so that the battlefield network is transformed from a force multiplier into a force exponent. The ultimate objective is to see farther with greater clarity and to act faster with more precision than one’s adversary while denying the other side the ability to do the same.
Five Elements
The battle network is made up of five functional elements each with a combination of personnel, platforms, processes and technology to carry out a given task. Some of the platforms and payloads can be part of multiple functional elements simultaneously. These elements are:
Sensor element: The first element comprises the sensors, both active and passive, to collect data. This data is used to detect and geolocate forces, identify and classify them as friendly or hostile. The sensors are also used to assess the effectiveness of actions taken, that is battle damage assessment.
Communications element: It provides the data links that pass information among systems and operators. The information transmitted can include voice, video, one-way data broadcasts or two-way data links.
Processing element: This is one of the most critical components of a battle network. It is used to analyse, aggregate and synthesise data from a variety of sensor sources to inform decisions. A key discriminator in the processing element is where the processing occurs: on-board the sensor, in the cloud or at the tactical edge. The platforms that carry some sensors may also have sufficient size, weight and power (SWAP) to carry the computational components needed to process the data they produce before transmitting it. Cloud-based processing offers the advantage of essentially unlimited processing and data storage capacity without the SWAP limitations of many platforms. Sensors can transmit raw or partially processed information to data centres on the ground for final processing and analysis.
Decision element: This is the most important part of the battle network because it is where information is translated into action. Where the decision is taken, how it is made, and who is involved depends on what types of actions are being considered. For the foreseeable future, major decisions such as the use of lethal force, will likely involve a human-in-the-loop at some level. Human-in-the-loop decision-making can still involve many forms of computer-assisted or artificial intelligence and machine learning (AI/ML) augmented processes to better inform decisions and accelerate the process, e.g. all engagements beyond visual range already use computer-assisted decision-making.
Effects element: The fifth and final element of a battle network is where information is turned into effects in the battlespace. These effects include both kinetic fires, which physically damage or destroy adversary forces, and non-kinetic fires, such as electronic warfare, directed energy weapons or cyberattacks.
To function effectively, these elements should have interoperability between all sub-systems, immunity to disruption with very high redundancy. Only then will the commanders be able to rapidly understand the battlespace, direct their forces faster than the enemy and deliver synchronised combat effects across all domains to achieve the desired end state.

Current Networks
The current battlefield networks in service range from the India’s project Shakti to Russian battle network. Some of these are:
India: Shakti, a fully digitised, integrated and networked Artillery Combat Command and Control System (ACCCS) was the first among the various Combat Command Control and Information (C3I) systems fielded in the Army. It is a network of military-grade tactical computers automating and providing decision support for all operational aspects of artillery functions from the corps down to the battery level. The system is also designed to seamlessly integrate with overall C3I grid. The other systems are the air defence control and reporting system, battlefield surveillance system and battlefield management system.
Russia: Since initiating the reform of the Russian Armed Forces in 2008, Moscow has developed a limited network-centric warfare capability that was tried out first in Syria. It places emphasis on force enablers and force multipliers like the electronic warfare (EW) capacity and a unified reconnaissance and intelligence capability. Russia had created a unified command-and-control (C2) structure as part of the National Defence Management Center (Natsionalnomu Tsentru Upravleniya Oboronoy—NTsUO) in Moscow that lies at the heart of Russia’s network-centric capability.
The NTsUO acts as an information hub, facilitating all military operations in real time, managing all military subunits in the Russian Armed Forces, including the nuclear triad. It unites the various automated C2 systems functioning across the Armed Forces. Consequently, the NTsUO includes three command-and-control centres uniting the various automated C2 systems: the Strategic Nuclear Forces Command and Control Centre, the Battle Management Centre and a Centre for Management of Day-to-Day Activities. Despite the impressive structure, the Russian network has serious limitations especially in the use of military communications and reconnaissance satellites as has been experienced in the Russo-Ukraine conflict.
China: China perceives modern military conflict as a confrontation between opposing operational systems that is waged not only in the traditional physical domains of land, sea and air but also in outer space and the nonphysical cognitive, cyberspace, and electromagnetic domains. To execute such a concept, the Chinese have been developing an integrated ‘system confrontation’ approach to operations since 2005 that is akin to but broader than US network-centric warfare. The PLA’s aim for creating an informatised force is to build a system of systems that can coordinate activities across the military and inside and between military theatres, arms, and services. The central warfighting system in this concept is the operational system, a linkage of organisations, functional processes and networks enabling integrated joint service warfighting across all domains. The operational system is made up of five component systems: the command system, firepower strike system, information confrontation system, reconnaissance-intelligence system, and support system.

Within this, the Network Systems Department of PLA Strategic Support Forces (SSF) is a theatre command-level organization responsible for information warfare with a mission set that includes cyberwarfare, technical reconnaissance, electronic warfare, and psychological warfare.
China is now moving towards ‘intelligentised’ approach to warfare away from its ‘informationised’ approach to warfare by harnessing emerging technologies such as artificial intelligence, cloud computing, big-data analytics, quantum information and unmanned systems that will enable her to carry out faster processing and the fusing of information for quicker decision-making and command-and-control efforts to support future combat operations.
United States: The battlefield networks include the Advanced Battle Management System (ABMS) of the United States Air Force, which started out as a replacement for the E-8C Joint Surveillance Target Attack Radar System (JSTARS) aircraft and has evolved into a secure, military digital network environment. The US also has the Terrestrial Layer System, which is intended to network a range of sensors—including intelligence agency sensors—to enable precision kinetic, electronic and cyberattacks. One system that it started operationalising is the Integrated Battle Command System (IBCS). It was initially planned to be used against regional ballistic missile threats but has now a wider role of integrating a broader array of sensors and shooters to counter cruise missiles and unmanned aircraft threat as well.
Severe Limitations
Most of the current battlefield networks have severe operational limitations. Designed for military operations of yore, they are not optimised for speed, complexity and lethality of future conflicts. The networks have limitation in terms of range and complexity of sensors as the decades-old platforms cannot adequately leverage new technology even currently available.
Lack of interoperability between various systems is a major limitation as services specific networks rarely have the ability to communicate with each other. Another limitation of the current battlefield networks is that it either does not have the supporting structures to enable future C2 or they require maturation.
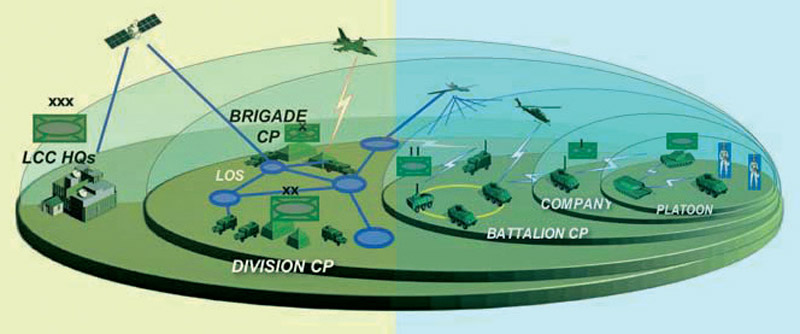
Next Gen Networks
The battlefield networks that can meet the needs of the future force have been enabled largely by technological advances that have taken place in recent decades. It is a point of interest that these advancements have been driven in part by commercial developments: lighter, cheaper and higher fidelity sensors; increases in data throughput capacity and coverage from cellular, fibre, and satellite communications networks; massive cloud computing and data storage centres; and big data analytics, machine learning (ML), and artificial intelligence (AI) systems.
The application of these commercial technologies to military battle networks has manifested itself in whole or in part in many different concepts, initiatives, strategies and buzzwords over the years. This long line of thinking includes the Revolution in Military Affairs and what the Soviet’s termed the Long-Range Reconnaissance-Strike Complex in the 1980s and 1990s; the Transformation Initiative, Network-Centric Warfare, and the Third Offset Strategy of the 2010s (to name a few examples). Realising the importance of harnessing the civil technological advancements, China has formalised the process with its Military-Civil Fusion (MCF) Development Strategy to ensure more effective flow of dual-use technological innovation into the defence sector. One key area where such a technology is proposed to be used is the development of the battlefield network.
Gathering Information
Starting from the first stage, gathering of information and access to data so collected is the first criticality. The information should not be corrupted and the network should have the capability to speedily process the intelligence data collected to translate it into actionable information.
As the battlefield network will incorporate both new and legacy systems, it should ensure interoperability not only between the sub-systems but also between the networks of different services. For instance, the air force network should be able to communicate and exchange information with the army’s networks, especially of the air defence.
A2/AD environment
The battlefield network should be able to securely and reliably connect sensors to shooters and support command and control in a lethal, electronic warfare-rich environment. The battlefield network itself will be a prime target for the enemy hence it should not only have immunity against soft kill but also the required redundancy against hard kill weapons as well. Also, the network should have the requisite technical maturity and affordability to be able to function in the future operating environment.
However, the biggest challenge is the military’s continued focus on platforms and not the network. Most of the focus remains on acquiring newer platforms that are visible and offer better optics than a network subsystem mounted on a truck.
Recent Developments
Russia has had the opportunity to battle test its networks, first in Syria and more recently during the ongoing conflict with Ukraine. There are reports that Russia has refined its Strelets-M Integrated Command and Communication System (ICCS) and the Andromeda-D battlefield management systems. These networking systems allow drone operators and other soldiers to input enemy positions and targets on a digital map, facilitating fighter aircraft, kamikaze drones, or artillery with guided shells to engage the targets with minimal delay.
Due to these improvements, Russia has been able to shorten the sensor-to-shooter kill chain and is largely succeeding in detecting Ukrainian attempts to its defensive lines well in time and frustrating the attempts to a great extent through the use of affordable and yet effective fire strikes using drones and guided artillery shells. Some of battlefield networks being developed and fielded by other countries are discussed below.
India: The Indian army is working on a number of key projects to enhance battlefield situational awareness within the framework of network-centric warfare. These projects include Project Sanjay, the new battlefield surveillance system that aims to provide an integrated surveillance picture to commanders and staff at all levels by integrating a large number of sensors and creating number of surveillance centres for the field formations. The project has already undergone field trials.
The other project is upgradation of the artillery combat command and control system (ACCCS) with highly accurate defence series maps, its integration with Project Sanjay will complete the sensor-shooter grid. Project E-Sitrep Situational Reporting Over Enterprise-Class GIS Platform (E-Sitrep) will take care of all operational correspondences in the army. These projects will be integrated to provide inputs to the new situational awareness module for the army (SAMA).
SAMA is a decision support mechanism that is designed to present a comprehensive battlefield picture to commanders at all levels. The aim of all these projects is to enable improved battlefield surveillance, faster decision making and appropriate weapon response using automated means and technology to meet future challenges.
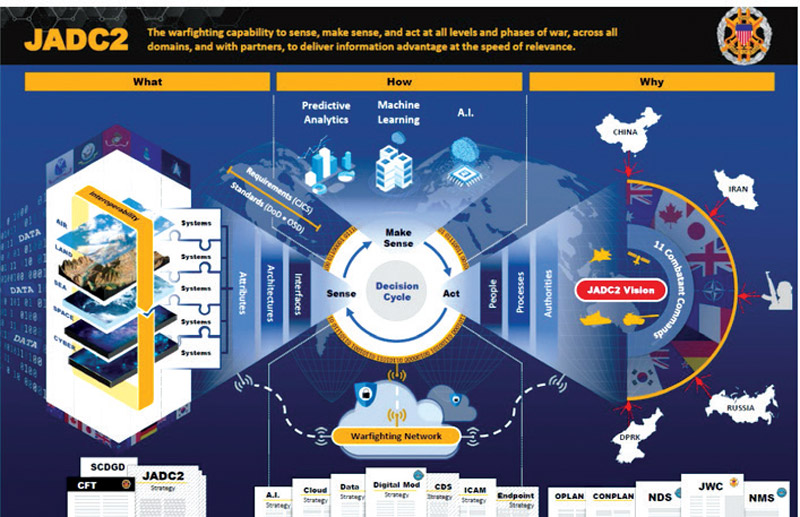
United States: Taking a different route, the US is developing an overreaching system called the Joint All Domain Command and Control (JADC2). This is in consonance with the transformation under way as the US prepares to fight near-peer adversaries in multidomain operations.
The JADC2 aims to connect sensors from all military services into a single network wherein a cloud-like environment is provided for the joint force to share intelligence, surveillance and reconnaissance data, transmitting across many communications networks to enable faster decision making. The JADC2 intends to enable commanders to make better decisions by collecting data from numerous sensors, processing the data using artificial intelligence algorithms to identify targets, then recommending the optimal weapon—both kinetic and non-kinetic (e.g., cyber or electronic weapons)—to engage the target.
China: The Chinese People’s Liberation Army (PLA) is developing its own battlefield network that is proposed to be a multi-domain network that can support its new operational concept called Multi-Domain Precision Warfare (MDPW) and also have the capability to disrupt, cripple or outright destroy an adversary’s underlying networks and infrastructure, specifically the US JADC2 initiative.
The MDPW aims to align all PLA forces, from cyber to space, and relies on interlinked command and control, communications, computers, intelligence, surveillance and reconnaissance to quickly coordinate firepower and expose foreign weaknesses. It is important to note that the PLA refers to “systems destruction warfare” as the next way to conduct war as warfare is no longer solely focused on the destruction of enemy forces; rather, it is aims to disrupt, cripple or outright destroy the other’s underlying networks and infrastructure.
Threats to Networks
Intelligence gathering is a fine art. It goes beyond UAVs sending back images to real and perceived targets. This aspect is important as almost all militaries across the globe are smitten with livestreaming i.e. live feeds being provided from the battle zone and being used to make decisions.
The belief that the image is the reality is a dangerous one with serious consequences as livestreaming has a very real tendency of affecting perceptions and negatively influencing decision-making. It has also led to an overreliance on UAVs and livestreaming at the cost of other assets. Unless checked, this can lead to changes in operational behaviour to satisfy the hunger for pictures – at the cost of achieving real objectives. The battlefield networks should be so designed that undue credence is not given to imagery at the cost of other inputs.
The efficacy of any weapon or support system is directly dependent on the degree of integration into the battlefield network. Care should be taken to ensure that the degree of integration is optimal for all systems and sub-systems and it is not done in a haphazard or patchy manner thereby degrading the potential of the weapon (or support) system.
Network Competition
With advances in communications and computer technologies, the benefits associated with networking military systems have also increased at an affordable cost. But it has also increased the competition and conflict between capable, competent adversaries. As competencies increase, so do the threat from adversary networks. From indirect artillery fire techniques first developed in the late nineteenth century to the duel between the US Air Force and the Vietnamese integrated air defence system to the use of drones and electronic warfare systems in the Russia-Ukraine conflict, battle network competitions have always existed. In this battle of operating systems and networks, the adversary networks themselves have become the prime target.
The laned MDPW of China is a prime example of battlefield networks being developed to counter and degrade the adversaries’ network(s). This is an important aspect to bear in mind as the battlefield networks will not only need to compete against a hostile network but will be expected to still be able to function effectively.
Artificial Intelligence
While battlefield networks, particularly the air defence networks, already making use of artificial intelligence (AI) and Machine Learning (ML) to a limited extent, the use of AI/ML in battlefield networks will increase significantly in the years to come. AI/ML applications across the systems will allow for integration of larger number of sensors using robust communication paths to synthesise and process data into actionable information at machine speed. This in effect will create improved capabilities in information detection, identification and synthesis across multiple domains.
The capability of AI to processes vast amounts of information faster and more accurately is just one of the advantages of using AI in battlefield networks. It can ingest, process and synthesise vastly more information at superhuman speed while also predicting the outcomes of a potential course of action and evaluate environmental or adversarial variables that would be beyond human capacity to assess. Through its prediction capabilities, AI can identify and continue tracking a high-value target even when the target disappears from the line of sight. It can proactively mobilise kill platforms and carry out dynamic re-tasking of platforms.
AI has the ability to find connections between disparate pieces of information and by collating data across domains and services into a single place, it makes information more discoverable for swifter and sharper decisions. It has an added advantage that it can see ahead of the battlespace, giving commanders a cursory understanding of the environment beyond current capabilities and the ability to respond proactively rather than reactively.
Limitations Exposed
The technological advances and new-gen battlefield networks being tested across the globe seem to offer new capabilities to militaries but it is important to note that not all capabilities publicised or assessed translate into actual performance in battle.
This is best illustrated by looking at some prominent network failures in recent times, from the shooting down of an Indian Air Force helicopter by friendly fire in 2019 to the failure of the Russian C2 system in the initial phase of the conflict with Ukraine. Though Russia had invested heavily in upgrading its C2 capabilities and had even tested its networks in Syria, the Russian military was plagued by poor intelligence and reconnaissance capabilities in the early months.
For example, during the counteroffensive in Kharkiv, the Russian military often lost track of Ukrainian brigade elements, leading to the successful Ukrainian rout of Russian forces in the region. Moreover, each Combined Arms Army operated independently through its axes of advance, with little overall coordination. Russia faced major communications issues with even the Strelets reconnaissance, command-and-control, and communications system being targeted and disrupted early in the invasion. The loss of over 200 command posts and communication stations only added to the chaos and confusion.
Technological Dangers
It is often said that the nature of warfare has changed and recent technological advancements have made the present day and future wars much different from the conflicts of the past. Most of the scholars use the phrase “paradigm shift in the nature and spectrum of war” while discussing these changes and tend to focus on technology leading these changes as modern armies look deeper, process almost unlimited amount of data and strike farther than ever before. But these changes are not without their dangers, namely the overreliance on technology on the one hand and the failure to fully exploit the latest capabilities on the other.
An overreaching battlefield network that links all entities, provides limitless real-time information and images of far and beyond with multiple options being generated by AI driven sub-systems and weapon systems taking on real (and perceived) hostiles, like the Skynet of Terminator series may be desirable and attainable, but unless it is managed and controlled with the required human intervention, it may well become the nemesis. The battlefield networks thus need to be designed and developed with due care so that they are the solution rather than a part of the problem.
It also needs to be remembered that technology alone will never be able to solve all the problems of command and control as an advancement is often accompanied with unexpected complications and side effects or by the inevitable rise of effective countermeasures. It is true for all technological advances. And it is true for battlefield networks. The need is thus to be ready for the changes and advancements by being ahead of the curve for only those who harness and exploit these changes will survive in the future battlespace.

