Being a victim of state sponsored cyberattacks, India needs to invest in cyberwarfare
 Smith Gonsalves
Smith Gonsalves
Cyberwarfare is an effective way of disrupting the functioning of a nation-state. It has the potential to impact the economy, connectivity, and even political stability of a country. An insidious aspect of cyberwarfare is cyber intelligence that can compromise both national interests and nation security.
Targeted Cyber Attacks on India
Akin to guerrilla warfare, the enemy is unknown in cyberwarfare, hence direct contact with it is not possible. It is often said that cyberwarfare is bloodless with the ability to have kinetic impact on foreign territory without physical operations.
The following infographic shows how attacks are carried on people with the use of different techniques such as profiling, target selection, intrusion areas like email address and phone numbers etc. There are various methods and techniques to carry simulated attack chains with the use of mitre attack framework for offence and defence.
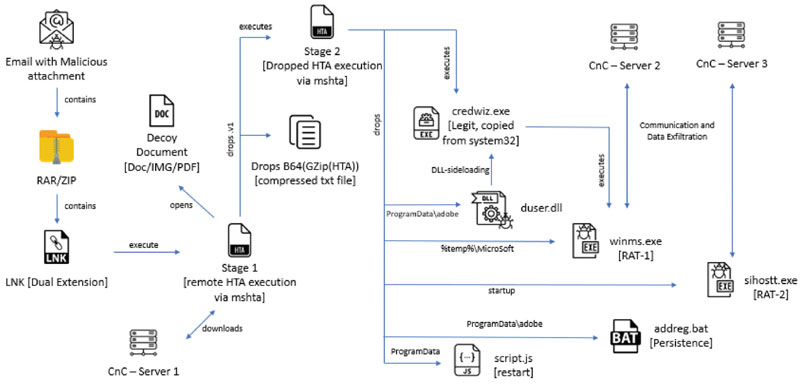
Analysing more specifically, we can see in the following infographic how a targeted Advanced Persistent Threat (APT) campaign operates through sending a malicious email which when clicked can take various privileges and establish Command and Control for transferring confidential files to the attacker’s system from the moment attachment is downloaded to its escalated execution on the system.
These are active APT campaigns used by Pakistan and China units to trick government and military personnel.
As we go deeper into the preparedness of India’s cyber strategy for combating–defensively and offensively–state sponsored cyber-attacks, we must understand the challenge we face. The truth is India has been facing continuous cyberattacks by its adversaries. Some of the instances of cyber terrorism are:
1) A malware was identified in the Kudankulam Nuclear Power Plant.
2) Cosmos Bank was hacked by North Korea’s APT groups.
3) Mumbai’s power grid was targeted by Chinese hacker group Red Echo.
4) Prominent corporate and government enterprises have suffered data breaches. They have faced both ransom and hostage situations at the time of ransomware attacks.
5) A targeted drone attack on the air force station in Jammu with kinetic payloads attached and operated through a remote command and control was seen in June 2021.
6) Transfer of data across international boundaries by adversarial state-owned companies.
7) Continuous use of perception management, misinformation and disinformation campaigns on social media platforms by Pakistan’s DG-ISPR operatives.
8) Honey trapping of soldiers and government servants to steal confidential information.
9) Purchase and sale of national identities like PAN, Aadhar, Driving License, Passport & KYC Data on Dark Web by cyber syndicates.
10) Cultivation of dead cells and multi-level marketing pushed into larger sections of people to fund adversarial intelligence operatives via social media applications.
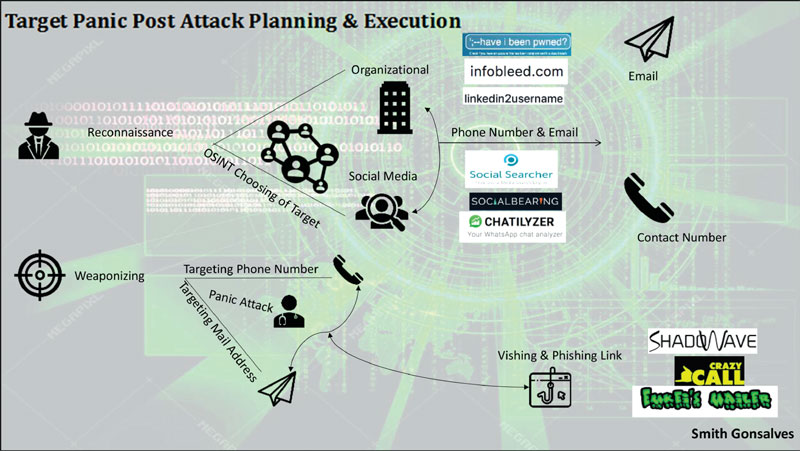
Clearly, Indian infrastructure is vulnerable to the state-sponsored attacks generated mainly from Pakistan, China, North Korea and Turkey, as well as non-state actors. The countries targeting India have been very clear both in their modus operandi and the gains they intend.
Meanwhile, India has been quietly pushing certain cyber reforms to modernise its cyber capability. While achieving smaller objectives, it misses the bigger picture. For example, India has got an advantage in countering the misinformation campaign run by Pakistan. It also has better control on Pakistan-centric cyber intelligence. This has been possible because of the investment in time and strategy build-up for more than a decade.
This is also because India has the capability of interlaying human intelligence (HUMINT) with Open-source intelligence (OSINT) available on the internet. This has been one of the key factors in formulating India’s strategy against misinformation campaigns. However, this approach does not work in closed countries like China, where the language alone presents a major challenge in developing HUMINT and Technical Intelligence (TECHINT).
India’s Offensive Defence Strategy
With its Belt & Road Initiative, China’s has also started sharing its closed source platforms with allies like Pakistan and North Korea. Also, in countries like Nepal, it has imposed Mandarin as a second language. Given this, if we don’t develop our cyber capability making it China-centric, there is a possibility that we might lose the HUMINT and TECHINT advantage developed against Pakistan as well. The reason is simple. Algorithms and security products incubated in China once shared with its allies will provide the same resilience to them as they do to China.
A pointer to this was the Pulwama attack. A lot of Indian hacker groups or Hacktivists launched a series of defacement campaigns against the Pakistani government websites, which hitherto were infamously vulnerable to attacks. However, this time, once such attacks were launched, Pakistan deployed Web Application Firewalls coded in Mandarin!
Apart from that, these state-sponsored attacks also have their micro level implications on work from home environments.
The Counter
Both our strategic offence to counter adversary’s defence and our own defence capability build-up are equally important. Achieving this balance would take us on the path of a robust security setup. While defensive cybersecurity technologies are available off-the-shelf worldwide, with some global original equipment manufacturers (OEMs) even offer modular systems with open architecture. But the problem is cost. Since the threat is invisible, both private enterprises and government organisations are reluctant to spend too much money on cyber fortifications. This lack of allocation of necessary budget to modernise the cyber defence inventory leads to avoidable vulnerabilities.
The government must be faulted for not holding accountable the tech companies who sell snake oil in the name of security products at 10 times the costs. Because of this, organisations tend to buy cheaper goods. That’s where China has an edge. Security is a multi-billion-dollar industry, worldwide. What matters is investment in solutions. The companies which do so remain resilient towards attacks.
Here are a few steps that the government must take to ensure minimum cyber defence capabilities:
1) A standardised cost barriers on foreign solutions.
2) Equal importance towards Indian start-ups with alternative solutions.
3) Fund raising and defence accelerators programmes for security companies.
4) War-time cooperation with private companies.
5) Civil military fusion for companies aiming to have global footprints.
6) Data Privacy Policy and Regulations with liability and penalties.
7) Standard Cyber Security Framework for entities operating in India.
8) Collaboration and coordination among law enforcement agencies for sharing cyber threat intelligence.
9) Mandatory KYC information for social media users to operate and removal of all the bots operating on the same numbers or emails.
10) Academia should do its bit by funding more research in the field of cybersecurity.
India has been quite introverted when it comes to showcasing cyber offensive capabilities. Of course, this approach is sensible for ensuring that smaller footprints are disclosed. Notwithstanding that, there are a series of roadblocks in having a stable approach. Every agency or organisation in India is tasked to operate within defined boundaries. Furthermore, these agencies have their own restrictions in communicating and sharing intelligence with other agencies. Hence, various blind spots are mishandled, as agencies work in silos. This is the biggest disadvantage when it comes to analysing adversarial capabilities.
Another important aspect to be looked at is the right and relevant skills. The good news is that the cyber security communities that have been doing tremendous coordination and commendable work to upskill their resources are expanding in India. However, the bad news is that these resources are quite young and have less experience. Therefore, they can inadvertently lead to disclosure of footprints on enemy boundaries, compromising the entire operation.
This is also because some of the entry level government officials aren’t very keen on supporting and guiding young resources. Instead, the officials are interested in having a short-term gain from the resource at a cheaper investment. Another wrong practice is hiring very young professionals in the age group of 18 to 22 years, to work on critical missions. They expect them to be excellent hackers which is unreasonable. No doubt these people possess skills and are willing to learn, but they also need to be trained on the backup plans, obfuscation and evasion tactics, which is only possible with a reasonable experience of around 10 to 12 years in the field of core memory development along with guidance from veterans.
This is one of the major reasons start-ups or highly skilled people aren’t well integrated with the government agencies. This use and throw behaviour impact upon the long-term development of cyber warfare capabilities.
India needs to be self-reliant as far as dependable offensive capability is concerned. Unlike traditional weapons like guns and ammunition that can be purchased from global OEMs, offensive cyber capabilities must be developed in-country. Not even an ally will share such information for analysis and operations purposes. Instead, the ally would work in joint teams on target-centric activities of a particular adversary just as the US and Israel collaborated on Stuxnet against Iran.

The offensive cyber capabilities that India should invest in includes:
- Capability to mine and weaponize ‘zero-day exploits’ on a continues scale and testing them in adversarial sandbox environments. A zero-day exploit is the method by which hackers attack a system or a software with previously unidentified vulnerability.
- Evolution of GAN (Generative Adversarial Networks) models for bypassing, obfuscation and mutating evasions.
- Creating persistent capabilities to stay undetected in adversarial networks with admin privileges for long term duration.
- Researching on bypassing situational awareness programmes of unmanned combat vehicles during war.
- Researching on hardware and memory level exploits specifically aiming at adversarial military communication networks like software defined radio’s (SDR), sensors and Electronic Warfare equipment.
- Use of AI patterns to trick and divert AI integrated command & control stations during war.
- Ability to gather data on adversary’s platforms and applications.
- Capability to develop and use quantum computing for breaking of complex encryptions.
- Real time anomaly detection for targeted OSINTs.
Since cyber warfare would bring the battlefront right into individual homes, combating it through both defensive and offensive means would need the ‘whole of nation’ approach. Government institutions and public sector enterprises will have to collaborate with private enterprises, especially the start-ups to create a robust cyber security environment in the country. No short-cuts here.
(The writer is a director and principal consultant in his start-up, CyberSmithSECURE, which specialises in providing cyber security services to MNCs and government agencies. He describes himself as a security evangelist)

